Prevent Social Engineering and Insider Threat Across Every Channel
Simulate attacks across email, SMS, voice, video, and encrypted apps, score user risk using integrated signals, and automatically prioritize remediation based on role and behavior.


Trusted by Fortune 1,000 Companies

.svg)






.svg)






.svg)







Security Awareness Training Is Broken.
Legacy SAT programs treat every employee the same, ignoring access levels, user behavior, and real-time risk, leaving you exposed to modern attacks.
Dune replaces ineffective training and static testing with live risk scoring, adaptive remediation, and automated defense, reducing user driven risk, strengthening security culture, and saving time across your organization.

User Adaptive Risk Management
Dune's User Adaptive Risk Management platform simulates multi-channel attacks, integrates behavioral and contextual data, and automatically adapts training, alerts, and controls to each individual’s risk profile to prevent user-driven breaches.
Risk Inputs
Risk Remediation
Business Impact
Agentic Attack Simulations
Training Activity
External Security Integrations
Historical and Custom Data
Executive Reporting
Delivers clean, high-level insights into user risk, threat exposure, and security posture.
Exposure Prioritization
Escalates remediation for high-risk users to focus action and save time on low-risk users.
Most Users
User Adaptive Training
Highest Risk Users (5%)
Access Restrictions
Dynamic Enforcement
Performance Management
Measure User Risk
Quantify individual user exposure by combining AI-driven context analysis, behavioral signals, and simulation performance. Identify which users are most likely to cause a breach.
- Real-time insight into breach risk
- Behavioral and contextual signals
- Remediation prioritized by exposure
Simulate Attacks
Launch continuous, omni-channel simulations – spear phishing, smishing, deepfakes, and encrypted threats – tailored to each user to expose attack susceptibility and insider risk.
- Omni-channel red teaming
- User-specific, real-world attack paths
- Measurable behavioral insights
Reduce Threat Exposure
Automatically adapt training, alerts, and controls based on each user’s behavior and risk profile. Minimize friction for low-risk users while escalating protection where needed.
- Risk-aligned microtraining per user
- Automated IAM & SecOps triggers
- Real-time enforcement & remediation
Business Impact
Evaluates each user's role, level, and function to calculate potential breach impact on the organization.
Omni-Channel Attacks
Simulates social engineering attacks via spear phishing, SMS smishing, voice call vishing, and encrypted-channel attacks.
Training Activity
Captures user engagement and sentiment across just-in-time training, compliance, functional, and org-specific training.
External Security Integrations
Ingests unlimited signals from your security stack (IAM, SEG, EDR, DLP, HRIS, and more) to build a single, continuously updated view of each user’s real-world exposure.
Historical Data
Pulls in users' historic testing and training data from previous SAT and user risk platforms to create a contextual baseline for risk scoring.
User Adaptive Training
Delivers just-in-time training tailored to each user's behavior, risk profile, and role.
Access Restrictions
Triggers access restriction workflows when a user’s risk score exceeds defined policy thresholds.
Adaptive Enforcement
Surfaces risk-based enforcement recommendations and routes them to the appropriate control systems.
Performance Management
Gives leadership real-time, comprehensive visibility into the highest-risk users, with prioritized risk data and actionable context.
Executive Reporting
Delivers clean, high-level insights into user risk, threat exposure, and security posture.
Exposure Prioritization
Escalates remediation for high-risk users to focus action and save time on low-risk users.
How Dune Secures the User Layer
Modern attacks are conversational, cross-channel, and invisible to legacy tools. Dune closes that exposure gap and acts in real-time. Dune delivers continuous visibility into how attackers reach users, identifies which users create the most risk, prioritizes exposures, and automatically remediates user risk as threats unfold.

Attackers exploit conversations across email, SMS, voice, video, and encrypted messaging apps to manipulate users and bypass traditional controls.
Dune continuously simulates real-world social engineering attacks across every communication channel users rely on, including SMS and encrypted apps like WhatsApp, Viber, Signal, and Telegram. These simulations mirror how modern attackers operate, using multi-step interactions and impersonation tactics that adapt based on user responses.
Wherever attackers can reach users, Dune exposes those risks so you focus on securing who matters most.
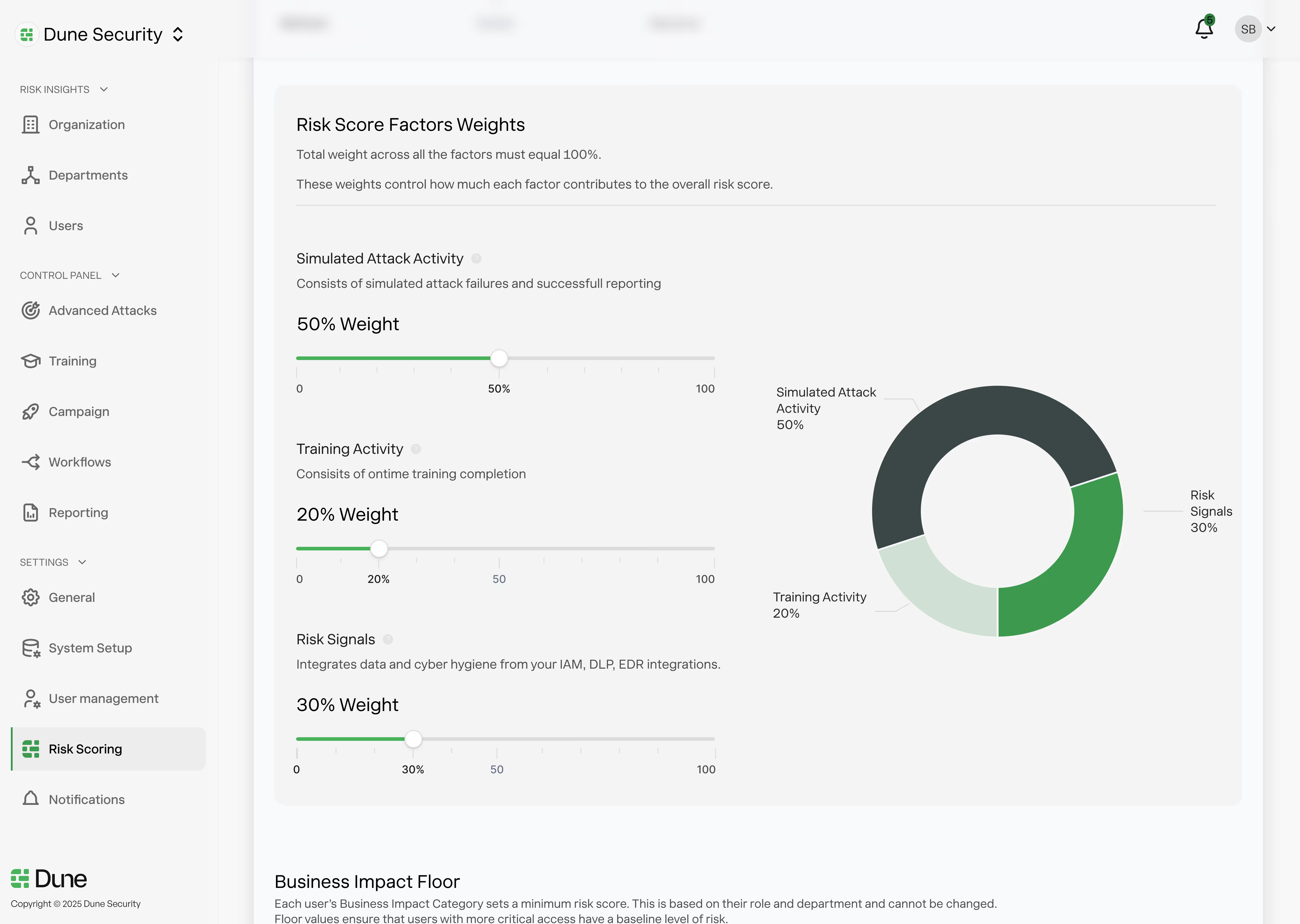
Not all users create the same level of risk. Identifying the highest risk users requires more than a single signal.
Dune calculates dynamic, user-level risk scores by combining multiple real-world risk inputs. These include vulnerability to omni-channel attacks, user behavior during live simulations, training activity and engagement, role-based business impact, signals from existing security integrations, and relevant historical data.
By correlating these inputs in real-time, Dune shows which users are most likely to be exploited and which compromises would have the greatest business impact. This allows security teams to focus attention on the small percentage of users driving the majority of organizational risk.
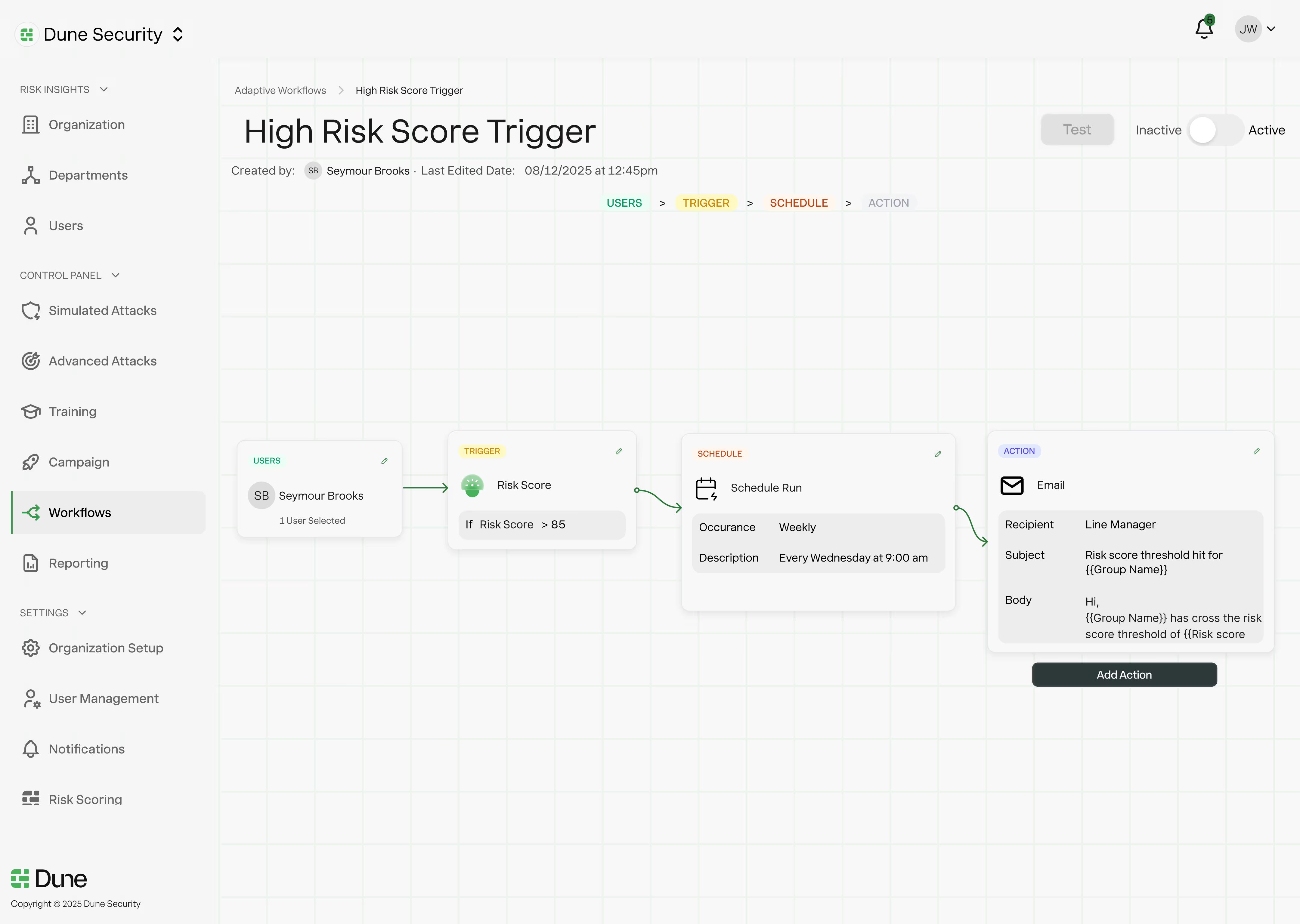
User risk is not static, and remediation should not rely on manual follow-up or one-size-fits-all training.
Dune automatically remediates user risk by adapting simulations, delivering targeted training, and triggering security workflows based on real behavior. When users demonstrate elevated risk, Dune increases testing, delivers role and behavior-specific microtraining, and applies the appropriate security controls. When risk decreases, friction is reduced.
Training is delivered only when and where it is needed, informed by how users actually behave under real attack conditions. This approach reinforces secure behavior without training fatigue and ensures remediation scales automatically across the organization.

Integrations
.avif)









Scalable and secure for the world’s largest companies
Frameworks

Certified – Jan 2024 & Jan 2025

Certified – Aug 2024

Compliance Verified – Jan 2025

Compliance Verified – Jan 2025

Third-Party Attested – Apr 2025

Third-Party Attested – May 2025
Ready to protect your company & employees from social engineering attacks?

Security Leadership That Understands Enterprise Risk
Testimonials
reduction in average user risk scores through targeted training that cut exposure across 90+ countries.
less time spent managing training logistics by automating workflows and eliminating manual overhead.
increase in detection of social engineering vulnerabilities with adaptive simulations that exposed hidden risks.

of manual training replaced with automated, role-specific modules tailored for higher education.
weeks less time spent managing training logistics by automating workflows and eliminating manual overhead.
month to achieve full visibility into user and department-level risk for the first time across the organization.

reduction in user risk scores projected within 45 days through localized, role and risk-specific micro-training.
increase in training completion and engagement rates as employees began actively interacting with simulations.
languages launched within one month to scale global security awareness with high adoption


Why Dune Security Wins
Feature | Dune Security | Next-Gen SAT | Legacy SAT |
|---|---|---|---|
Real-Time User Risk Scoring |  | – | – |
| Behavioral & Role-Based Risk Signals |  | – | – |
| Automated, Risk-Based Security Controls |  | – | – |
| Seamless Integration Across IAM, SEG, EDR & DLP |  | – | – |
| GenAI-Powered, Role-Specific Attack Simulation |  |  | – |
| Adaptive, Just-in-Time Security Training |  |  | – |
| Admin Automation & Real-Time Risk Reporting |  |  | – |
FAQs

A real-time security model that scores user behavior, simulates threats, and adapts controls to reduce human-layer risk.

By analyzing behavior, running GenAI-powered simulations, and ingesting risk signals from your IAM, EDR, and email stack.

Yes—Dune integrates via API with IAM, SEG, EDR, and DLP platforms for full-stack coverage and fast deployment.

Yes—Dune replaces static SAT with adaptive training, delivered only to risky users and triggered by real behavior.

Dune targets actual risk. Instead of training every user equally, it scores behavior, simulates threats, and adapts controls in real time.

Most teams are live in days. Our platform integrates easily and includes guided onboarding from security experts.

Yes—Dune provides real-time reporting to support GDPR, CCPA, HIPAA, and other frameworks across users, roles, and regions.
Ready to see Dune Security in action?
"We can't keep doing the same thing and expect different results. Dune Security is doing something new and exciting, and they’re showing quantifiable outcomes."

Jeremy Livingston













.avif)
























